2017
10 Ways You Can Tell if Your Phone Has Been Hacked
Tips
As the old saying goes, once the genie is out of the bottle, there’s no way to put him back. That’s how creator of the internet, Sir Tim Berners-Lee, has recently stated he feels about the worldwide web which he gifted to the world.
He has warned that the potential for mobile phones and other devices to be tampered with in far reaching and damaging ways is high if proper protection is overlooked. “When people are thinking about the security of their systems, they worry about people discovering what they are doing,” Tim Berners-Lee said. “What they don’t think about is the possibility of things being changed.”
Citing an example, he said: “If you disrupted traffic data to tell everybody that all the roads south of the river are closed, so everybody would go north of the river, that would cause gridlock and disable the city,”
With iPhones and Androids rapidly becoming more advanced, there’s a growing trend in the number of smart phones being hacked, leaving users extremely vulnerable to compromised personal information. But what are the tell-tale signs your mobile phone has been compromised? If you notice any of the following occurrences over the course of a few days, the chances are your device has been hacked or compromised.
1. You have recently noticed your smartphone is slow and clunky

If your mobile feels like your phone is working reluctantly, almost against your will, and is slow, unresponsive, and typing is difficult, it may have become infected with malware. There are a number of free apps out there that can slow down your phone’s performance, and quickly fill the memory on your phone. Review your apps carefully, and if there are any you don’t need, or are not sure about, delete them.
2. You’re sending or receiving unusual text messages

If friends start telling you they are receiving unusual and unwanted text messages from you, or if you are receiving such messages, you could have had a security breach. It’s time to run a reliable anti-malware app to check if there is a problem.
3. New apps have been added to your phone and you didn’t install them

There are several vulnerabilities in operating systems that may let Android or iOS malware escalate privileges and gain the ability to circumvent security features. This can result in apps being installed without your permission. These apps can potentially steal your data, record your calls and text messages. They can even hijack your social-media and online banking sessions. Immediately delete any apps you did not install.
4. The battery is draining much quicker than it used to
Malware chews up battery time as it works on code in the background. If you find your battery draining faster than it used to, check your apps to see how much memory they are consuming. If necessary delete them and install again, or just do without them. A clean fast phone is one that is not overloaded with apps.
5. Certain apps have stopped working properly
When apps that were working perfectly well, start to misbehave, delete them, run a virus and malware check and install again from a trusted third party.
6. Data or text messaging (SMS) is greatly increased but your usage remains the same
You know your monthly data usage, but lately it has been considerably higher than you expected. Beware of text messages that can arrive in your inbox inviting you to click on them. Some of these seemingly innocent texts can charge you for every text you receive, and you can receive several a day, which will massively affect your charges as these are premium rate texts. Delete any texts you do not recognize.
7. Charges you do not recognize are displaying on your phone

Criminals love nothing more than to exploit an infected device. They make expensive overseas phone calls via remote party proxying through your device. They can also send SMS messages to international numbers, or ring up charges in other ways.
8. Your phone has been accessing dodgy sites you never tried to view

Many business mobiles operate on private networks that ban dubious sites of a certain nature such as porn sites or pirated content sites. If you notice that your phone has been trying to access such sites and has been blocked, when you yourself have not attempted to visit them, it is more than likely your phone has been infected, and you should report it to the company’s IT Department before the finger of suspicion falls on you.
9. An acquaintance seems strangely well informed about your schedule/activities

If you feel someone knows more about you than they should, such as what time you will be at a certain venue, or certain comments you have made to other friends, you may be being cyber stalked. This means a piece of malware has been introduced to your phone for the purposes of discovering everything about your personal, and quite possibly your financial life, too. Again, this you need to protect yourself by running anti-virus and malware software from a trusted source. It may also be necessary to go the whole way and restore the phone to factory settings, but make sure you back up valuable information, music and pictures to the cloud before doing so.
10. Your phone number is all a hacker needs
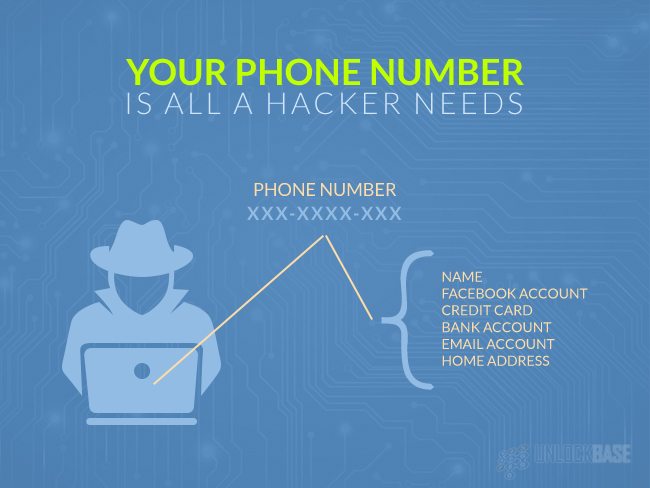
While it is important to take precautions by regularly checking your phone for malware and viruses, it is also worth bearing in mind that all a determined hacker needs to access your phone is your phone number. We are all guilty of giving away our mobile number too freely. How many business cards do you give to little known acquaintances during the course of the day?
Did you know an experienced hacker can use a network interchange service called Signalling System No. 7 (SS7), also known as C7 in the UK or CCSS7 in the USA.
CCSS7 acts as a broker between mobile phone networks. As calls or text messages are made across networks, CCSS7 handles details such as number translation, SMS transfer, billing and other back-end duties that connect one network or caller to another. By gaining access to the CCSS7 system, hackers can track a target’s location based on mobile phone mast triangulation, read their sent and received text messages, and log, record and listen into their phone calls, simply by using their phone number as an identifier. For this reason, it’s important to be extremely careful to whom you give your number.
How do you protect your mobile device when it has also become your mobile bank, your wallet, social network and more?
The truth is, you can never be fully protected, but an awareness of what hackers might try to do, and what happens when they have successfully hacked your phone will give you the awareness to do something about it quickly.
How can you change your service provider if you’re not happy with the service you’re getting?
That’s much easier to answer. Just contact Unlockbase. We have the largest database of mobile phones and service providers internationally. We can quickly, easily and securely unlock your phone and set you free to choose the best provider for your needs.
All products, and company names, logos, and service marks (collectively the "Trademarks") displayed are registered® and/or unregistered trademarks™ of their respective owners. The authors of this web site are not sponsored by or affiliated with any of the third-party trade mark or third-party registered trade mark owners, and make no representations about them, their owners, their products or services.

Comments are closed.