2018
16 Things You Should Know About Digital Privacy Invasion
Tips, UnlockBase
TL;DR
- Google is collecting data about you through your phone.
- Phishing comes in so many forms.
- Never trust your password to anyone, not even your phone.
- Use Password Managers.
- Change your passwords regularly.
- Add an extra layer of lock to your phone.
- Clean your browsers more often (than your house).
- Don’t just click “OK” or “I agree” absentmindedly.
- Employ 2FA (2 Factor Authentication) for all withdrawals (and on all your online accounts).
- Check the fidelity of your Social Media accounts.
- Create A Guest Wifi Network.
- Install a Firewall on your computer or on your home network.
- Use a VPN to hide your ass.
- Avoid using public Wi-Fi.
- Install manufacturer updates when needed.
- Be careful with the apps you install.
When we think about privacy in the digital world, we all suddenly feel anxious. Are we truly safe from privacy invasion? Are our phones especially equipped to keep our bank details, emails, phone numbers, etc free from hackers and digital thieves?
We’ve heard enough stories from people who lost their money because of email phishing and of those whose private videos got exposed and never got their peace again. It’s adding up to the anxiety people are burdened with nowadays, even after the extraordinary layer of security technology has to offer.
Mobile phones in particular, is one of the most vulnerable gadgets that is prone to hacker attacks. It gets especially hotter nowadays, since more and more people are using their mobile phones to buy things online, and even purchase products right off the shelves at Walmart.
Although mobile phones have become the best boon for humankind, it could also be the source of our greatest bane. With all the threats that’s going on around us, what can you do or what do you need to know to keep yourself safe when using your phone?
Well, let’s delve deeper and discover what you should know and what you can do to protect your privacy and essentially, your life.
1. Google is collecting data about you through your phone.

Did you know that you are being stalked by Google? Google knows almost everything about you. It can predict with absolute accuracy what you want to buy, what you want to search about, and even tell you where you’ve been last.
Google’s AI helps them know what ads to suggest based on your search behavior. And on your phone, there’s a default Google app that lets them know your location so they can suggest the best restaurants, places to visit, and report accurate temperature.
Ever since GPS, it was possible for anyone to follow us around or stalk without us knowing, and of course, this is a government initiative through NASA. Your mobile phone picks up signal from your mobile phone service provider towers and they can predict with almost perfect accuracy where you are at the moment just by using that data alone.
By default, Android and iOS users have GPS trackers enabled, but there’s no need to sulk, you can disable these location trackers just as easily. Here’s how to stop your phone from logging your location:
To Disable location reporting on Android:
- Go to Settings
- Location
- Google Location Settings
- Switch slider off on both Location Reporting and Location History
- Delete Location History
- Repeat process on each Google Account on your device.
Note that by disabling these services you are essentially limiting Google on suggesting information that may be of help to you. Nonetheless, you can leave Location Reporting on when you think you need it. You can also block Google from seeing your location through the help of a VPN app for Android devices from services like ExpressVPN. This not only blocks Google, but also your ISP from seeing your location.
To Disable location reporting in iOS:
- Go to Settings
- Privacy
- Location Services
- Swipe slider off on all apps or select apps you want it disabled (e.g Google Maps)
- System Services
- Deny location data from features you want to disable it
Note that with iOS you can’t erase the location history, so you have to log on to a web browser for you to do that. Choose the days you want to delete location history and you’re done.
2. Phishing comes in so many forms.

Bet you’ve probably seen how phishing emails look like, and hopefully it wasn’t successful on whatever its scheming to do. Email phishing disguises itself as a trustworthy organization aiming to gather important information from people who aren’t suspecting. They can disguise to be your bank, a famous brand, Google, and even your phone’s manufacturer!
Even Facebook has had this incident and a lot of accounts in so many countries had been infected. If you suspect your computer or your phone had been infected or hacked through Facebook or any other website, you can run a malware scan and immediately log out from the internet.
Unfortunately, hackers and phishers evolve fast and they are extremely creative. Nonetheless, it’s easy to outsmart them if you know how they really do it. Now, take a look at these examples:
- Pop-up offering quick fixes for your mobile problems. They can show you a result of a quick device scan and will ask you to download or install a malware that is potentially dangerous to your computer and/or the data in it.
- Email disguised to be your bank account asking for more account information. Your bank already has your account number, so there’s no way they’d ask that from you via email. Also, legitimate companies will not ask you to send your personal information through email or text.
- A Facebook message from a friend with a link. Facebook hackers have made it to your friends’ inbox and if your friend unsuspectingly clicks on that link, all the person on their friends list will receive the message as well. This links will slow your computer down or install extensions on your browsers that can gather login information. You wouldn’t notice they installed anything but when you login to your bank, email, or work-related sites using the infected browser, it will send the information to the hacker’s server.
- Emails disguised as customer complaint. High-level executives are the target of “customer complaint” phishers. They can even come up with an official-looking subpoena to make it look legitimate. More often, they are going to ask you to click a link where you will be asked to install a software so you can proceed. They can sometimes also clone your email login page where you will unsuspectingly enter your email login information to proceed.
- Emails disguised as a shipping carrier asking for your personal information. Key here is not to provide your address or any information about you if you can’t confirm you have an order with them. Most carriers don’t really need to confirm shipping information because it is done by their vendor or the company where you purchase your goods from. If you are not expecting any order delivery, better to erase it right away.
- Clone emails. As the term itself defines, this type of phishing clones or copies the exact email sent to you by a legitimate entity (e.g bank) and they also use an email address that looks like that of your bank. If you receive an email regarding a matter that your bank already had informed you with before, please don’t click any link. Instead investigate and verify the email by searching about it. You’re probably not the first to receive that email and the public have already been alerted about it.
- Email from an unknown company about a freebie or a voucher you can claim by clicking a link. Well, it is easy to bait someone using their emotion, but remember, if the offer is too good to be true, it probably is.
- Unsecured website login page. If you are routed to a page where you have to enter login information like username, email, pin, or passwords, always remember to check its security. Websites which as HTTPS and has a lock icon before the web address is safe and secure for you to enter your credentials. If on the other hand, it is only an HTTP or there’s no lock icon, you should be concerned. Also, you can check the website’s security certificate when you click on the lock icon. This helps you know how your data is protected.
Remember that phishing doesn’t only use one medium of communication. It can disguise itself as an unsuspecting text message from your daughter about your credit card information, or it can be through a call. When you receive a phone call from a company XYZ and they are asking personal information about you (including your birthday) that’s already one form of phishing.
There are other ways to prevent phishing and we’ll go through them in the next sections.
3. Never trust your password to anyone, not even your phone.

As mentioned earlier, hackers and phishers have created ingenious ways to install extensions on your browsers with a single click. These extensions are triggered by certain websites, especially those where you enter login information. Although it would be easier for you to keep your passwords saved or “remembered” by your browser, it would be unsafe for you to do that.
Google Chrome, for example, isn’t a secure place to store your passwords. Anyone with access to your browser can keep your login credentials and save it for their own use. Although the hacker has to have physical access to your computer for them to steal your login information, you surely don’t want them to discover something you want to hide or keep for yourself.
Your phone’s browsers are also flawed the same. You can keep your social media logins to yourself if you allow people to use your phone or borrow it. You can stay unsuspecting but better be safe than sorry.
4. Use Password Managers.
If you have way too many passwords for you to remember, you can install a password manager like Lastpass. You need only one master password for the software login and you can keep all of your passwords in there safe and sound.
You can set a two-way authentication as well, so that when you login using a computer, you will need to authenticate it using your phone or another gadget of your choice. There are a lot of free password managers out there, so go get one now!
5. Change your passwords regularly.

Talking about passwords, it is necessary that you change your passwords on a regular basis, especially for those which concern your privacy and your banking logins. Even Apple Pay has its own flaws, so never trust yourself enough to keep these passwords and PIN’s just the same for more than 6 months.
It is advisable that you change your credit card pins on a regular basis to protect yourself from card skimming. If on the other hand, you use your phone to purchase, you need to make sure that your phone is locked enough that when someone steals it, it would be practically useless.
Jailbreaking a phone is something that even a grade-school kid can do nowadays, so to help protect yourself from this kind of disaster, you need to add an extra layer of lock to your phone which we will discuss next.
6. Add an extra layer of lock to your phone.
Adding an extra layer of lock or security to your phone is going to help you not only secure your phone’s private data but it also prevents other people from using your information illegally.
There are a lot of free App Locks you can download from Google Play. With an extra lock installed you can lock certain apps and programs using a 6-digit PIN code and a simple toggle and voila, your Facebook, Gmail, or banking app is safe with another line of security.
Mobile phone manufacturers understand this necessity that’s why they always pack your devices with biometrics such as iris scanner, Face ID, fingerprint scanner, etc. However, no technology is perfect and there are still flaws in the system.
In an iPhone X, for example, your identical twin brother (if you have) can open your phone without any problem. In China, a lot of people had been in an uproar against Apple lately due to its racism in producing iPhone X.
A woman had discovered that her son can unlock her iPhone X and when she got to the store, she was told that there was a problem with the camera. She later discovered that everyone else can actually unlock her phone using their face with no problem and so was every other iPhone X in the store!
This major flaw had been denied by iPhone and of course, they denied the accusation of being racist. This had happened a month later iPhone X was released in the market.
7. Clean your browsers more often (than your house)

Cleaning your browser is as important as cleaning your house. You have to erase your browsing history once in a while if you want to keep your devices safe from hackers.
Although there is a need for any hacker to have physical access to the device (e.g mobile phone), once someone breaks into your computer, they can look at the browser history and use the available data to steal information from you.
It’s easy to clean your browser. If you are using Chrome on your phone:
- Go to Chrome app
- Tap More History
- Tap Clear browsing data
- Go to Browsing history
- Uncheck any other boxes you don’t want to delete.
- Tap Clear data
Clean your browser often and save yourself from dirty trouble in the future.
8. Don’t just click “OK”or “I agree” absentmindedly.

We all know that apps do ask “permissions” to access certain programs on your phone like your contacts, calendar, photos, messaging, notes, etc. By default, all of these programs have their boxes ticked, it’s up to you to uncheck the box next to the program you don’t want the app to have access with.
Limiting the app’s access isn’t going to affect the performance of the app, although there will be features that are to be compromised. Nonetheless, if you don’t want your Facebook, Messenger, Twitter or any other app for that matter have access to data that you think should stay private like Contacts, you can opt out and still be able to use them.
If you want to limit permissions on some apps, here’s what you need to do:
- Go to Settings
- Apps
- Device
- Tap the Gear icon
- App permissions
- Toggle slider ON or OFF on apps you want to limit access
In the same way, does some websites ask for permissions. If you have seen websites asking permission to “give you a notification about latest updates” or even asking to “enable cookies“, you better read what exactly they want from you.
By default, you shouldn’t allow them to do just that, and in fact, Google already penalizes websites who don’t let you opt out from these “permissions“. What these “cookies” do is to observe your behaviour when in the internet so they know what ads to suggest.
Amazon does this and so does other e-commerce websites. Google also does this, however, to a much healthier extent. When the information gathered by these cookies are given to the wrong hands, you’ll be spammed and the next thing you know, you’ll have annoying pop-ups every now and then.
If you are using Chrome on your computer, here’s how you change permission on all sites you will visit:
- On you computer, left click on Chrome
- Hover your mouse on the top right, click More (it looks like 3 bullets in a line)
- Click Settings
- Scroll down and click Advanced at the bottom
- Under “Privacy and Security” click on Content Settings
- Change the permission you want to update.
If you are using Android or iOS on your gadget, here’s how you get there:
- Open Chrome
- On the top right, click More (it looks like 3 bullets in a line)
- Hit Settings
- Under Advanced, tap Content Settings (iOS) or Site Settings (Android)
- Tap on the permission you wish to change.
- Please follow “Recommended” advise from Google Chrome but ideally, you would want the following to be on the corresponding mode:
- Cookies – Removing some cookies may mean that you will be logged out from some websites)
- Camera – Should be on “Always Ask” mode
- Location – “Ask before accessing”
- Microphone – “Ask before accessing”
- Notifications – “Ask before sending”
- Flash – “Ask first”
- Pop-up’s– “Blocked”
For more information regarding Chrome browser settings, you can visit Chrome Support or you can go here for the full tutorial on their support site.
9. Employ 2FA (2 Factor Authentication) for all withdrawals (and on all your online accounts)

One way to also add another level of security to your bank accounts, Paypal, etc. you can add a 2-factor Authentication for all withdrawals. What this do is to provide you a notification on your phone (you bring daily), to authenticate and allow the withdrawal or any transaction.
This will help you to validate and deny the transaction that’s at hand. This keeps your money safe because the hacker has to have a physical access of your phone in order to do the last half of their job.
You can add 2FA on Paypal, WordPress, Evernote, Lastpass, Dropbox, Slack, Amazon, WhatsApp, and on your social media accounts. Google Authenticator is one of the commonly used 2FA apps and it supports a hostful of websites and apps that you want to have extra security. Thankfully, there’s a Google Authenticator app for both Android and Apple.
It’s fairly easy to get the app working. Once downloaded, install the app on your phone and sync your phone and tablet. For a full tutorial on how it’s done on Android or iOS, you can go here.
Apple also has 2-step authentication verification procedures that will notify you of any iCloud access or any app access on your iPhone or Mac. If you want to enable it, here’s how:
On iOS:
- Go to Settings
- Sign in on iCloud
- Tap arrow on Apple ID
- Tap Password and Security
- Tap Turn ON Two-factor Authentication
On macOS:
- Go to System Preferences
- Sign in on iCloud
- Click Account details
- Click Security
- Click Turn ON Two-Factor Authentication
Microsoft is also on the same league, and it will add more security on your OneDrive, Skype, Xbox Live, etc. If you want to enable 2FA on your, you can look at this tutorial from Microsoft Support for guidance.
Google also has a 2FA capability and they have enabled email alerts by default so you can receive an email about new browser logins. If there’s a login on a new or unrecognized device, Google will let you know about it via email.
10. Check the fidelity of your Social Media accounts.
Your social media accounts are surely going to be a headache once hacked. People can steal your identity or use your private information to blackmail you. But as mentioned earlier, you can enable 2FA on each of your social media accounts to keep them protected.
For mobile-only app or service which do not have 2FA capability, you can enable login verification. Also, if you have logged in any of your social media account on another gadget, you need to remove or “forget” your password on those devices. With SnapChat, you can do this remotely using login verification. You can also generate a Recovery Key or Code for when your mobile device is stolen to protect your social media accounts.
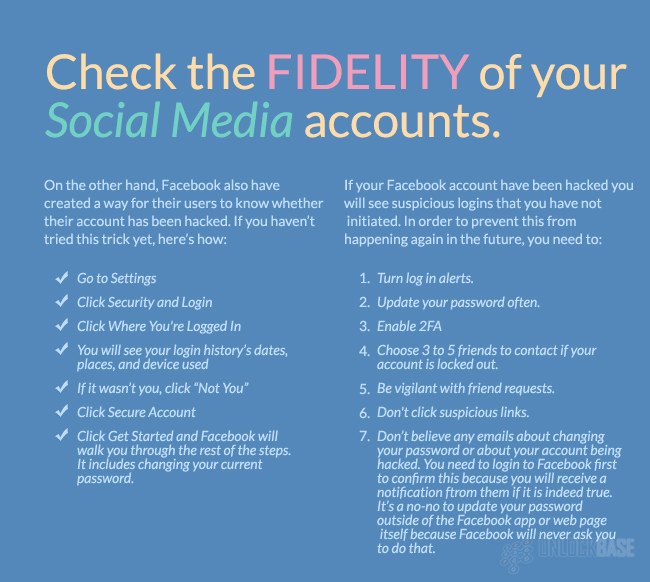
On the other hand, Facebook also have created a way for their users to know whether their account has been hacked. If you haven’t tried this trick yet, here’s how:
- Go to Settings
- Click Security and Login
- Click Where You’re Logged Into
- You will see your login history’s dates, places, and device used
- If it wasn’t you, click “Not You”
- Click Secure Account
- Click Get Started and Facebook will walk you through the rest of the steps. It includes changing your current password.
If your Facebook account have been hacked you will see suspicious logins that you have not initiated. In order to prevent this from happening again in the future, you need to:
- Turn log in alerts.
- Update your password often.
- Enable 2FA
- Choose 3 to 5 friends to contact if your account is locked out.
- Be vigilant with friend requests.
- Don’t click suspicious links.
- Don’t believe any emails about changing your password or about your account being hacked. You need to login to Facebook first to confirm this because you will receive a notification from them if it is indeed true. It’s a no-no to update your password outside of the Facebook app or web page itself because Facebook will never ask you to do that.
The same rule applies to every other social media account you have. Never assume your account is safe unless you did the extra mile of checking it. The information they can get from your Facebook or other social media accounts is enough to steal your peace and ruin your life.
11. Create A Guest Wifi Network

The struggle of having a connected home is keeping everything safe from thieves. If you have a connected home network, you don’t want anyone else to see or even remotely access your computer or gadget.
This is also one reason why, it is advised that you have a “Guest” Wifi network, so if your friends want to connect to your home Wifi when you hang out, they can do so without compromising your security.
If you have a connected home, it is important to keep all the access only to your trusted gadgets. Letting in an unauthorized mobile phone or laptop to your main Wifi network is dangerous because that means they can access your router’s login page and change the settings.
Whereas if they are connected to the guest network, they will not be able to access your router’s page. Thus, a guest network strengthens your network’s security.
They can get the IP addresses of your home’s main server where you store and share access to your important documents and data. Giving them access to your main Wifi is equal to giving them access to all of your house’s connected devices.
How do you create a Guest Network?
By default, most routers nowadays is already broadcasting a guest network and the main network using unique individual passwords. The guest Wifi network usually has a “-guest” suffix in the end. If you want to customize it, which is recommended, you need to know how to access the router’s setup page.
First, know your router’s brand name. The router is the device that transmits the internet connection coming from your modem into wireless signals. It’s practically the source of your Wifi connection.
There are also times when your modem and router is just one box, but if you aren’t sure which is which, you can ask your internet service provider to walk you through.
If you now know your router’s brand name, you can then search how to open it’s setup page, in most cases, all you need is your router’s IP address.
- Open browser.
- Enter your Router’s IP address.
- Enter router’s login information (username and password)
- Once logged in, look for the keywords Network, Guest Network, or Guest Access and click on it, or
- Click on “Allow Guest Access”
- Enter your preferred Wifi name on the SSID box.
- Enter your preferred Wifi password for your Guest network.
- Click OK or Finish.
And voila! Your guest network is already setup. If you can’t access your router’s setup page, you might need help from your internet service provider (ISP) or you can call the router’s manufacturer to walk you through.
There are a lot of high-tech routers nowadays and the router that came from your ISP is probably outdated and don’t have the guest network functionality. It is highly recommended you update it to the model that’s best for your family’s needs for wireless connectivity.
12. Install a Firewall on your computer or on your home network.

A firewall is one integral component to a home network. If you are using a cloud server in your home, you want that protected with a Firewall. A firewall can be a physical device or a software you can install.
Your router is one good example of a firewall. When you are connected to the modem, you will be given a public IP address and that is the perfect ingredient towards a hacking disaster. If you are using a public IP address you are like going to a war without an armor and of course, and we don’t want that.
To fully arm yourself, you need a firewall or a device or a software between you and the cruel world of the internet. Instead of using a public IP address, you want to use a private IP address.
The modem gives you a public IP address while the router in the other hand gives you a private IP address. With a router in between your device and the modem, hackers will not be able to get on your network and access your device.
It would be an extra challenge for them to hack your network because they will have to be connected to your private home network first before they can get in and start doing their business.
That being said, it takes your WiFi password for them to be able to steal information. With a well-secured router in your home, your network has better security.
Now, on the other hand, a Firewall could also be a software. You can install a software on your device to prevent it from getting viruses or malwares that can potentially harm the data that’s stored in your computer. These malwares can also be used to steal information from you and even shut your computer down.
If you want the best security for your home network and your devices, you need to have a strong Firewall.
13. Use a VPN to hide your ass.
A VPN or a Virtual Private Network is a medium or a service that serves two purposes:
- To remotely connect to your company/home computer
- To safely hide all of the data you transmit over the internet.
The security that VPN offers is best if you want to transmit or access private information over the internet. A VPN encrypts all the information that you use over the internet, so that you browsing history, downloads, etc will not be visible to your internet service provider.
If you are travelling or always on the go, you won’t fear the security threat of using a public WiFi because you can login to your VPN and open your emails securely without feeling like anyone is sniffing on you. Now, you can use the internet and no one will know what you accessed, downloaded, or seen because your internet service provider will not be able to take records of them.
You can hide your ass or your IP address and essentially be able to download via BitTorrent and save yourself from copyright infringement litigation. Just be sure to use a VPN that doesn’t have Europe, US, or Canada as their exit points where these activities are considered illegal.
You can also install a VPN on your mobile gadgets, so if you like the convenience of opening your email or your work CRM‘s using your phone or tablet, you can freely do so securely!
Although it used to be mainly for corporate use, a VPN is also a wonderful add on to your home network because of the security offers. The process is pretty straightforward as downloading an app (mobile) or a software (computer) to make it work.
Next, sign up for the service, you can choose between a paid and a free service, although the latter will probably sacrifice a little privacy from your end as they will feed you with ads according to your browsing behaviour, which is somehow a contradiction of the purpose it serves.
After signing up, be sure to read the EULA (End User License Agreement) because not all VPNs are created equal and you might be compromising an essential feature due to this trifling negligence. There are thousands of VPN service providers and choosing one can get overwhelming, but the top thing to consider is the reason why you are using it.
If security is one of the things you are most concerned of, then getting a VPN should be at the top of your list.
14. Avoid using public Wi-Fi.

As mentioned in the previous item, connecting to a public WiFi is a big no-no when you are trying to open your emails and even your social media accounts because this could potential put your privacy at risk.
If you are always on-the-go or can’t afford the cost of your postpaid service provider you can always have a VPN installed so you can keep yourself secured while on a public WiFi. You can’t expect for the speed to be fast though, as VPN connection uses a lot of data on encrypting your searches and may result to lower speeds.
Also, being on public WiFi means you are trusting the owner whatever information they get from your internet browsing data. If you have trust issues, don’t get yourself on a public WiFi.
Another alternative is to bring an unlocked portable WiFi hotspot which allows you to insert and use any sim from every country all over the globe. With your WiFi hotspot, you don’t need to connect to an unsecured public WiFi plus you can connect multiple devices and surf simultaneously on all these devices.
15. Install manufacturer updates when needed.

Alright, this is one thing that is pretty much done by your phone or computer automatically, however it’s not always like that. For instance, your gadget is probably going to ask your permission to install any updates where you can do later.
Every persistent hacker out there will always find a hole out of every software update and this is why manufacturers continue to produce update even after their flagship is out of the stores. Apple has been consistent in giving software updates for their phones however, Android manufacturers had been notoriously called out because they seem to stop giving updates after a new phone is launched. That doesn’t essentially mean Android is less secure than Apple, but the assurance of a consistent software update even after 2 years of purchase should be a part of your buying conditions.
16. Be careful with the apps you install.

Never ever download an app that is outside the official App Store or Google Play and that means you should only install apps from these places.
As mentioned in the earlier segment, apps ask permissions to get access to your mobile’s data, if you absentmindedly allow these apps to access anything they want to have access to, you just got yourself in to trouble.
The apps you download outside of the official Android and Apple stores are not tested by the software developers for security and they could potentially harm the data on your mobile by installing malwares or stealing vital information from it such as your contacts and calendar. It can even hack your email.
Stay away from sketchy app stores which offer apps you don’t see on the official app stores.
Takeaway
That was a whole lot of information about getting yourself safe in the internet both on mobile and on a computer, but the most important thing there is to remember is to always be vigilant and suspicious of everything you do online.
Be suspicious about the link, be very careful when you download, be vigilant when you grant app permissions, and be wary of suspicious websites. As the golden rule of thumb says, you’re better safe than sorry.
All products, and company names, logos, and service marks (collectively the "Trademarks") displayed are registered® and/or unregistered trademarks™ of their respective owners. The authors of this web site are not sponsored by or affiliated with any of the third-party trade mark or third-party registered trade mark owners, and make no representations about them, their owners, their products or services.

Comments are closed.